Development Process Safe and Secure with PILZ

April 27, 2022
TUV Sud scrutinized PILZ’s development processes. The result of this audit: PILZ’s development met the requirements of the standard IEC 62443-4-1 and complies with the SDL process. The international series of standards IEC 62443 “Industrial communication networks – Network and system security” deals with IT security in automation.
The range of topics spans from risk analysis, to requirements for safe operation and the secure development of products (security by design). As a result, IEC 62443 currently offers the best orientation guide for plant operators and device manufacturers when it comes to implementing security effectively.
It looks at five areas: the basic industrial security requirements, the principle of zones and conduits, the security levels, the security lifecycle and the risk analysis.
Product development is doubly safe, meeting the standard for industrial security
We are safety experts. It’s important to us that our products are not only safe, but also secure. That’s why we commissioned TÜV Süd to scrutinise our development processes and test them on the basis of the standard IEC 62443-4-1, which defines secure product development, the “Security Development Lifecycle Process” (SDL process). This approach examines potential security features, even as a new product is being designed. It is intended to ensure that all of a product’s security risks are detected by modelling the threats and, ideally, rectifying them in the product during the development process.
The result of this audit: Pilz’s development met the requirements of the standard and complies with the SDL process. As a result we can say with certainty: Pilz’s development is not only safe, but also secure!
According to TÜV Süd, the development of secure products in accordance with IEC 62443-4-1 is taken very seriously at Pilz and creates a solid basis for subsequent product certifications.
Basic industrial security requirements
The basic security requirements (foundational requirements) include:
- •Identification and authentication
- •Use control
- •System integrity
- •Data confidentiality
- •Restricted data flow
- •Timely response to events
- •Resource availability

For each of these foundational requirements further system requirements are defined, which can be used as a basis for the implementation of security measures.
Security level
Security levels define the security level that plant operators or manufacturers want to achieve using security measures. Information is provided by a prior risk assessment. This defines what is to be protected and determines the probability of this asset being attacked. The security level (SL) is selected accordingly. SL-2, that is protection against “intentional violation using simple means with low resources, generic skills and low motivation” should be seen as a minimum standard today.
To keep this minimum standard, the company needs a specific security maturity level. The best firewall is useless if a company’s employees continue to write their passwords on post-it notes and stick them on their PC screens or if they do not run updates. The more the company is involved in security as an issue, the higher the overall protection will be. Therefore an overall security concept is important. The application firewall SecurityBridge can contribute to a high security level as part of an overall concept.
The security levels at a glance:
Security Level 1: Protection against casual or coincidental violation
Security Level 2: Protection against intentional violation using simple means.
Security Level 3: Protection against intentional violation using sophisticated means
Security Level 4: Protection against intentional violation using sophisticated means with extended resources
Industrial security risk assessment
The security development process is an expansion of the general product development process. One basic aspect of a standard-compliant development process (in accordance with IEC 62443-4-1 – Secure product development lifecycle requirements) is to perform a risk assessment. It reveals the dangers and risks that a product is subjected to from “cyber space” and the measures to take to minimise them.
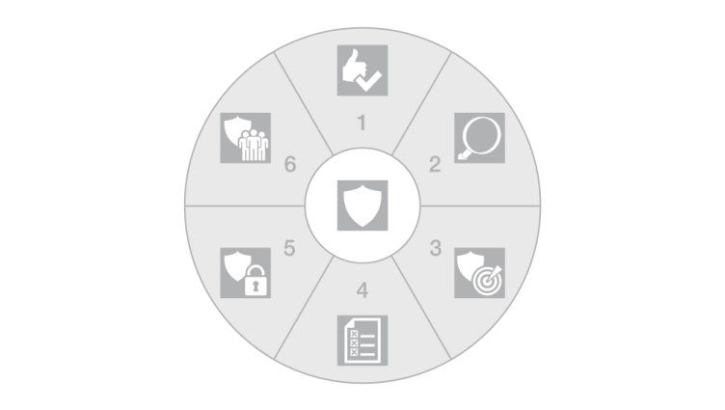
The security risk assessment should always be performed in the following 6 steps:
- Identify assets: What do I want to protect?
- Analyse threats: What are the risks on the asset I want to protect?
- Determine relevant protection objectives: What objectives do I want to achieve?
- Analyse and assess risks: How likely is it that a risk will occur?
- Select and implement protective measures: How can I protect from possible risks?
- Resilience management: What to do after an attack? How can I anchor the idea of security more firmly in the company?
Industrial security lifecycle
Security is a “moving target”, that is, security changes during a product’s lifecycle. Attackers develop increasingly better methods to overcome defence measures, so defence measures against cyber threats have to be improved continuously. The responsibility for this lies primarily with plant operators. An effective security strategy can increase the service life of your plant. Machine builders and component manufacturers should immediately inform the operators about new security problems. You must provide updates for your device’s software to enable customers to remedy any weaknesses. If system integrators are involved in the process, they act as an intermediary between manufacturer and operator. It is important that everyone involved works in close collaboration throughout the entire product lifecycle. Only this will result in a high degree of protection.
To learn more about Security 4.0 from PILZ, click here




